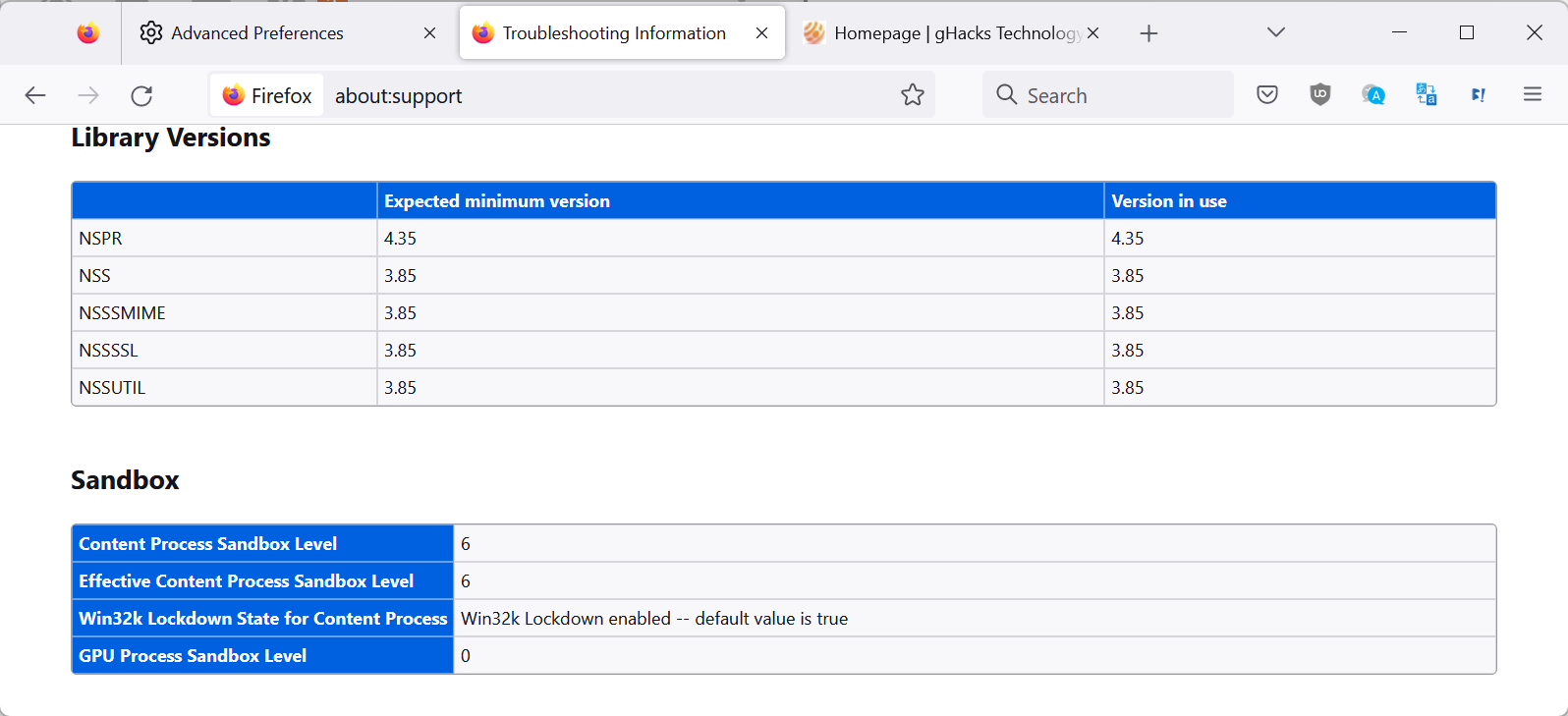
Proceedings of the 30th Annual International Conference on Computer Science and Software Engineering: Investigation of encrypted

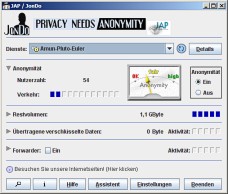
PDF) Dependable Networks and Services : 6th IFIP WG 6.6 International Conference on Autonomous Infrastructure, Management, and Security, AIMS 2012, Luxembourg, Luxembourg, June 4-8, 2012. Proceedings